Discovered nice cookie banner at the Security Now website.

Also, nice details on cookies at What are cookies?
The windows root
Discovered nice cookie banner at the Security Now website.

Also, nice details on cookies at What are cookies?
Received this popup today on my Windows Desktop from the Teams malware:
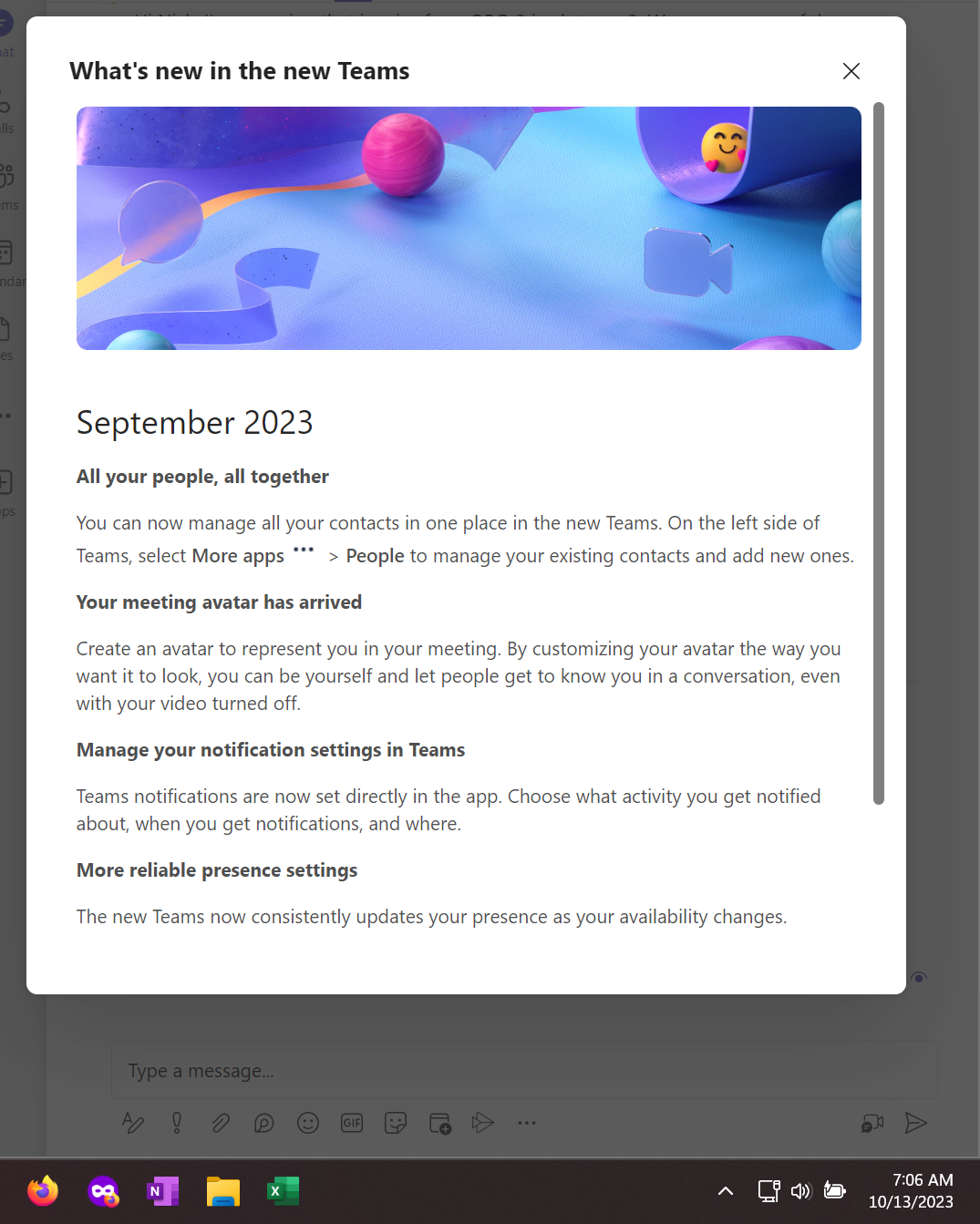
Thanks, but it is October 13th. WTF?!?!
Azure Arc Setup is now on my servers and I don’t remember asking or installing it!!!
Good take here by C:Amie (not) Com!
Start menu item:
System tray/notification area item:

Chrome reset
Close all chrome.exe instnaces
Go to folder %USERPROFILE%\AppData\Local\Google\Chrome
Rename folder User Data to User Data.old
Launch Chrome
Chrome cache folder: %USERPROFILE%\AppData\Local\Google\Chrome\User Data\Default\Cache
Computer\HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
command prompt or modern terminal
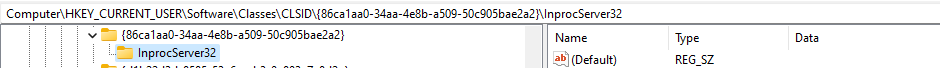
reg.exe add “HKCU\Software\Classes\CLSID\{86ca1aa0-34aa-4e8b-a509-50c905bae2a2}\InprocServer32” /f /ve
or
Computer\HKEY_CURRENT_USER\Software\Classes\CLSID\{86ca1aa0-34aa-4e8b-a509-50c905bae2a2}\InprocServer32
Useful tip from VMware
Enable content Copy/Paste between VMRC client and Windows/Linux Virtual Machine (57122)
Trouble:

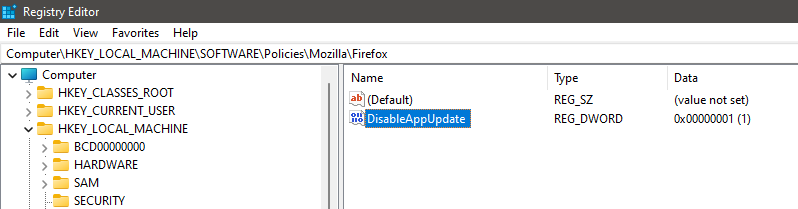
Fix:

Device in Azure AD showing “Pending” for Registered state for some time.
Admin command prompt: dsregcmd /debug /leave
Restart computer
Wait for Azure Active Directory Connect synchronization services (Azure AD Connect sync) to sync device before adding to Intune MDM.
Assist to ITProMentor.
VMware has released patches that address a new critical security advisory, VMSA-2021-0010 (CVE-2021-21985 & CVE-2021-21986). This needs your immediate attention if you are using vCenter Server (if you didn’t get an email about it, please subscribe to our Security Advisories mailing list). In most cases a security advisory is straightforward, but sometimes there are nuances that are worth extra discussion. That is the case here, and the goal of this post is to help you decide your course forward.
To get started, load up the DVD you want to rip and start up VLC. Then, under Media, click on Convert/Save.

The Open Media window will appear and you want to click on the the Disc tab.

Check the DVD box, and make sure that the “Disc Device” field points to your DVD drive. Click the Convert/Save button to rip the DVD.

You may also want to select “No disc menus” here, since VLC can occasionally get tripped up trying to convert a looping video menu.
There are a few other settings here you can tweak, too. Under Starting Position, you can choose which title and chapter you want to rip. If you’re interested in ripping special features, or just part of the movie, you can change these settings, but if you just want the movie, you can leave this at the default. Under Audio and Subtitles, you can similarly choose which audio and subtitle track you want to rip. If you’d prefer to grab a language other than the default or include embedded subtitles, you can choose them here. To change any of these four settings, type in the number of the track, title, or chapter you want to start with. You may need to do some trial and error to figure out which track is the one you want.
Once you click Convert, you can choose what type of codec and container you want to use to encode your rip. By default, VLC will choose an H.264 video codec, MP3 audio format, in an MP4 container. This preset should work for any DVD, but if you want to change anything, click the Tools icon to the left of the Profile drop down box.
When you’re satisfied with your profile choice (or if you want to stick with the default), click Browse to pick a name and location for your file.

Pick where you want to output your video file, then give it a name. At the end, be sure to include the file extension (in this case, .mp4). If you don’t include this, VLC won’t rip the movie properly. When you’re done, click Save.

Back on the Convert screen, click Start to begin ripping the movie.

Once it begins, you can see a progress bar along the bottom. Technically, VLC is “streaming” the video to a file on your hard drive, so it will take the entire runtime of the movie to rip it. Once the movie is done (or if you want to stop it early), click the Stop button.

As we said earlier, this isn’t the most robust way to rip a DVD, but if you just need to do a quick rip with the tools you already have on your computer and don’t need to fiddle with codecs or video quality—and don’t want to pay for a better ripping tool—VLC can do it just fine.
SOURCE:
https://www.howtogeek.com/howto/2696/how-to-rip-dvds-with-vlc/